ReAct, short for Reasoning and Acting, is a paradigm for enhancing large language models (LLMs) by integrating verbal reasoning traces with task-specific actions. Introduced in a 2022 paper, it addresses limitations in chain-of-thought (CoT) prompting by allowing models to interact with external environments, such as APIs or databases, to gather real-time data. This makes LLMs more reliable for tasks requiring factual accuracy or multi-step planning.
In the evolving field of artificial intelligence, large language models (LLMs) have transformed how we approach problem-solving, but they often struggle with hallucinations—generating plausible but incorrect information—or handling tasks requiring real-world interaction. Enter ReAct (Reasoning and Acting), a prompting framework that synergizes reasoning traces with actionable steps, enabling LLMs to behave more like intelligent agents. This detailed blog explores ReAct’s foundations, mechanics, advantages, and practical implementation, culminating in a sample Python application using LangChain. We’ll draw on established research and code examples to provide a comprehensive guide, updated with insights as of 2025.
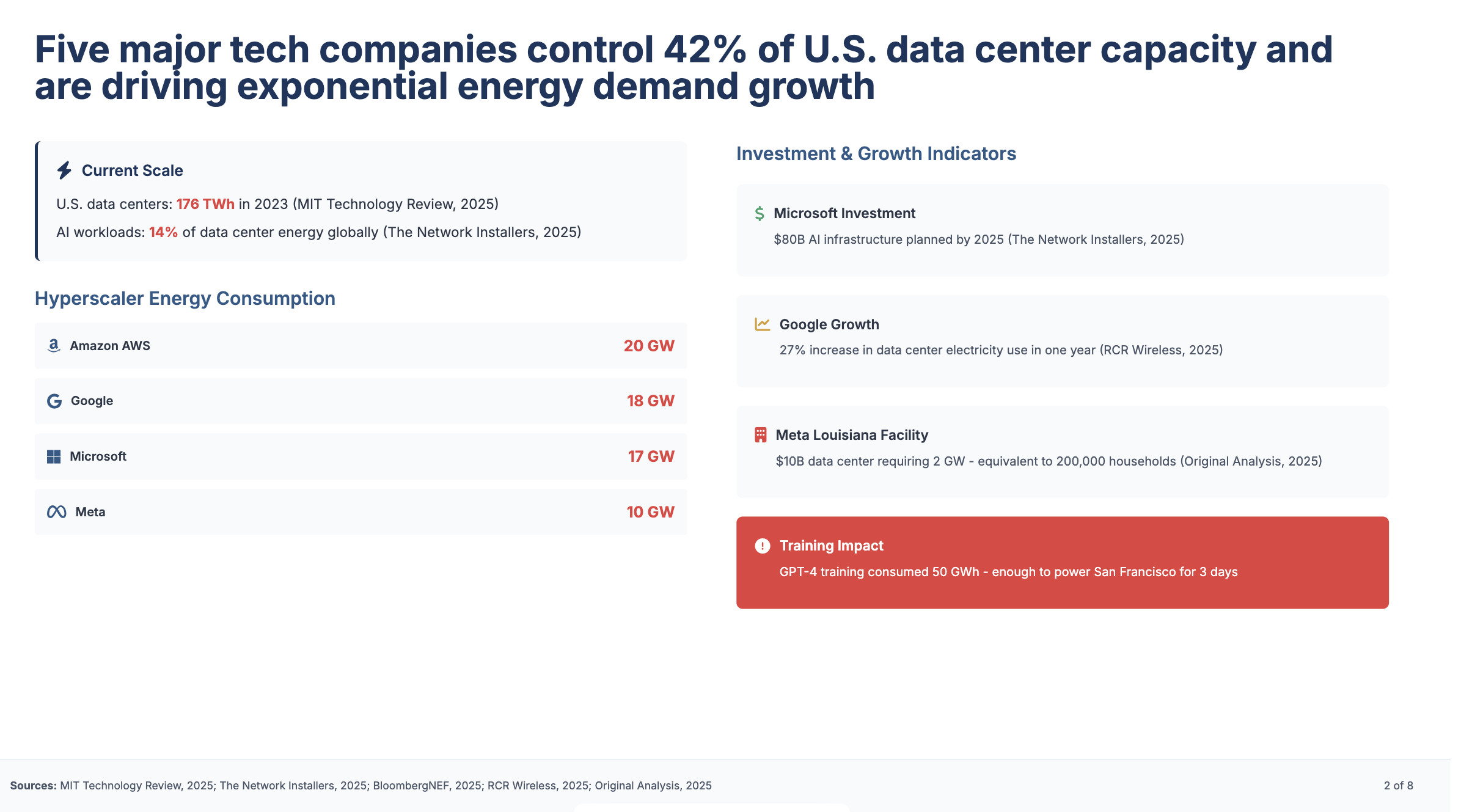
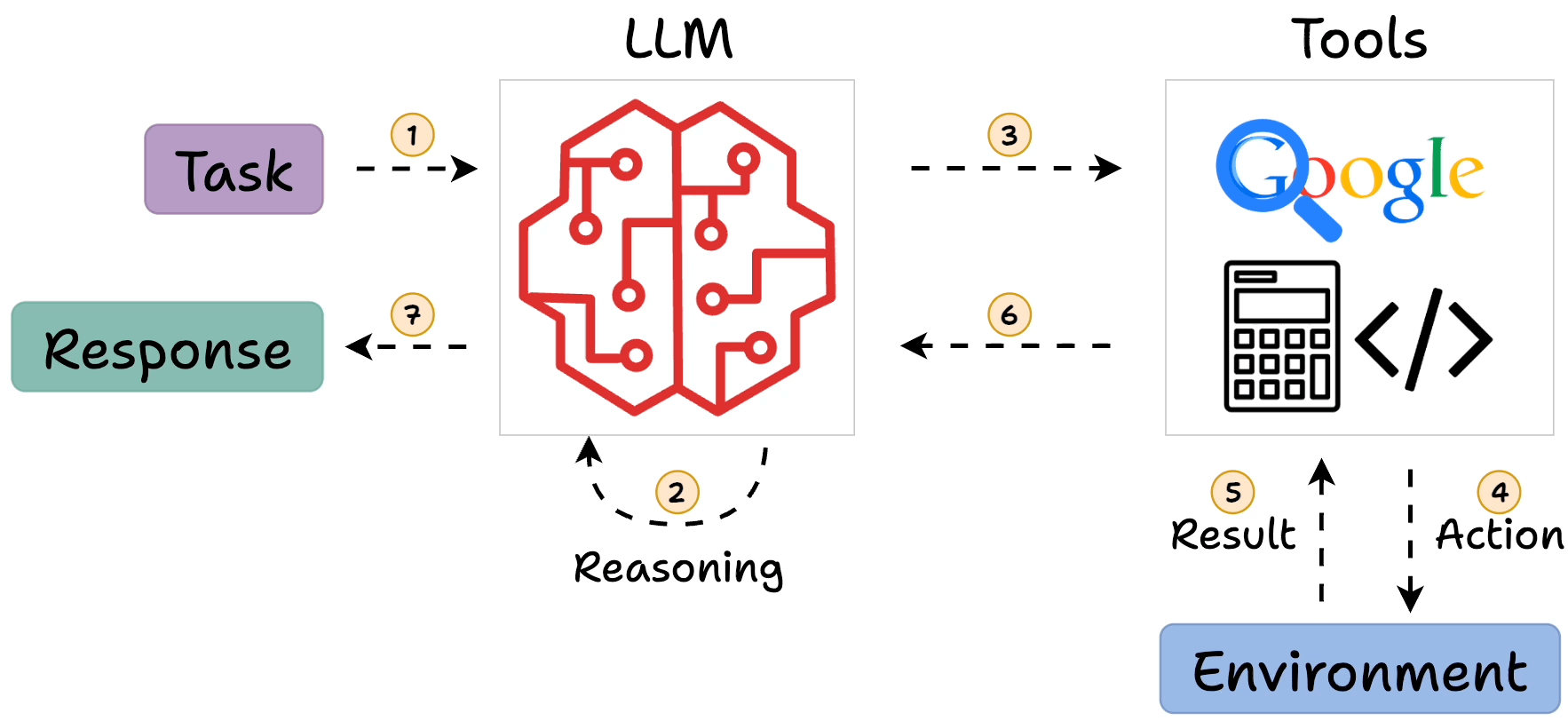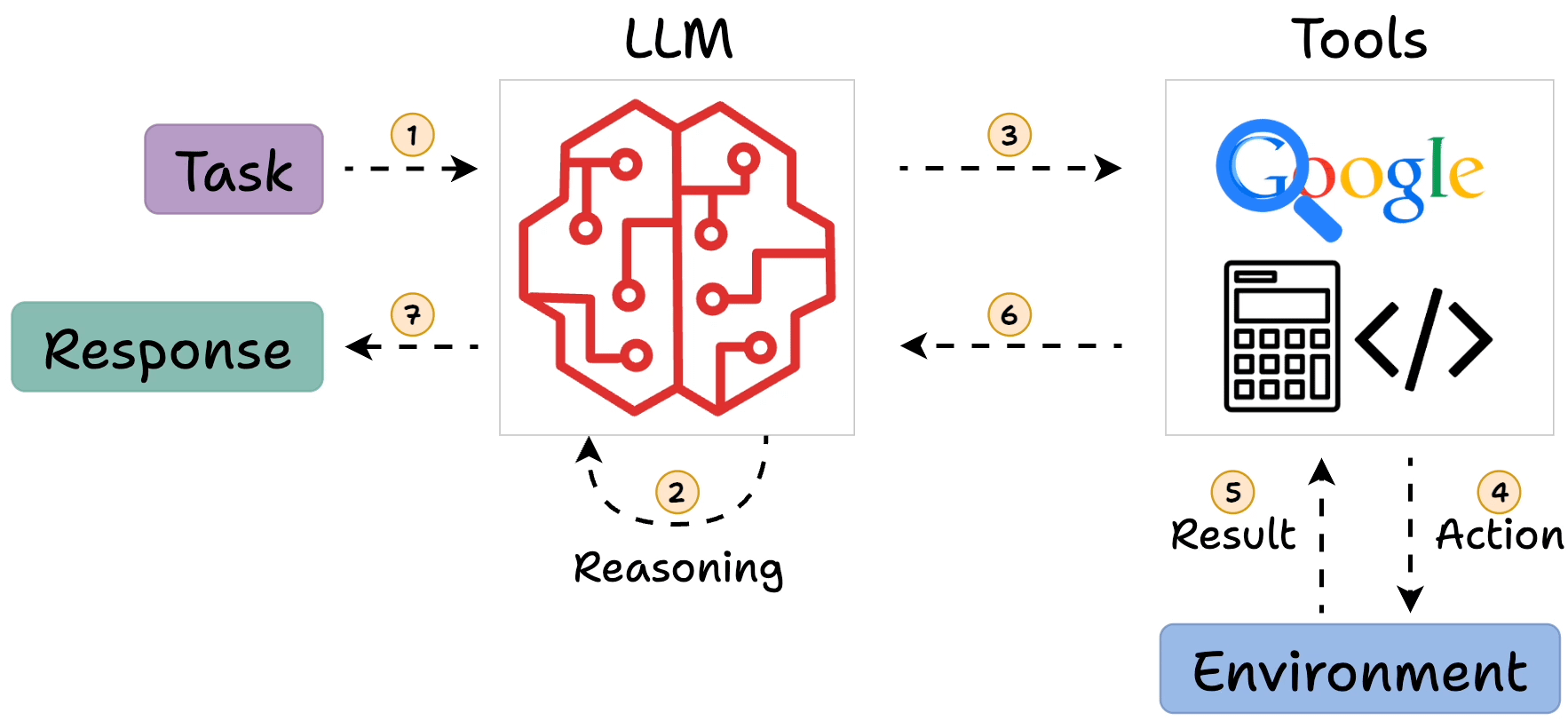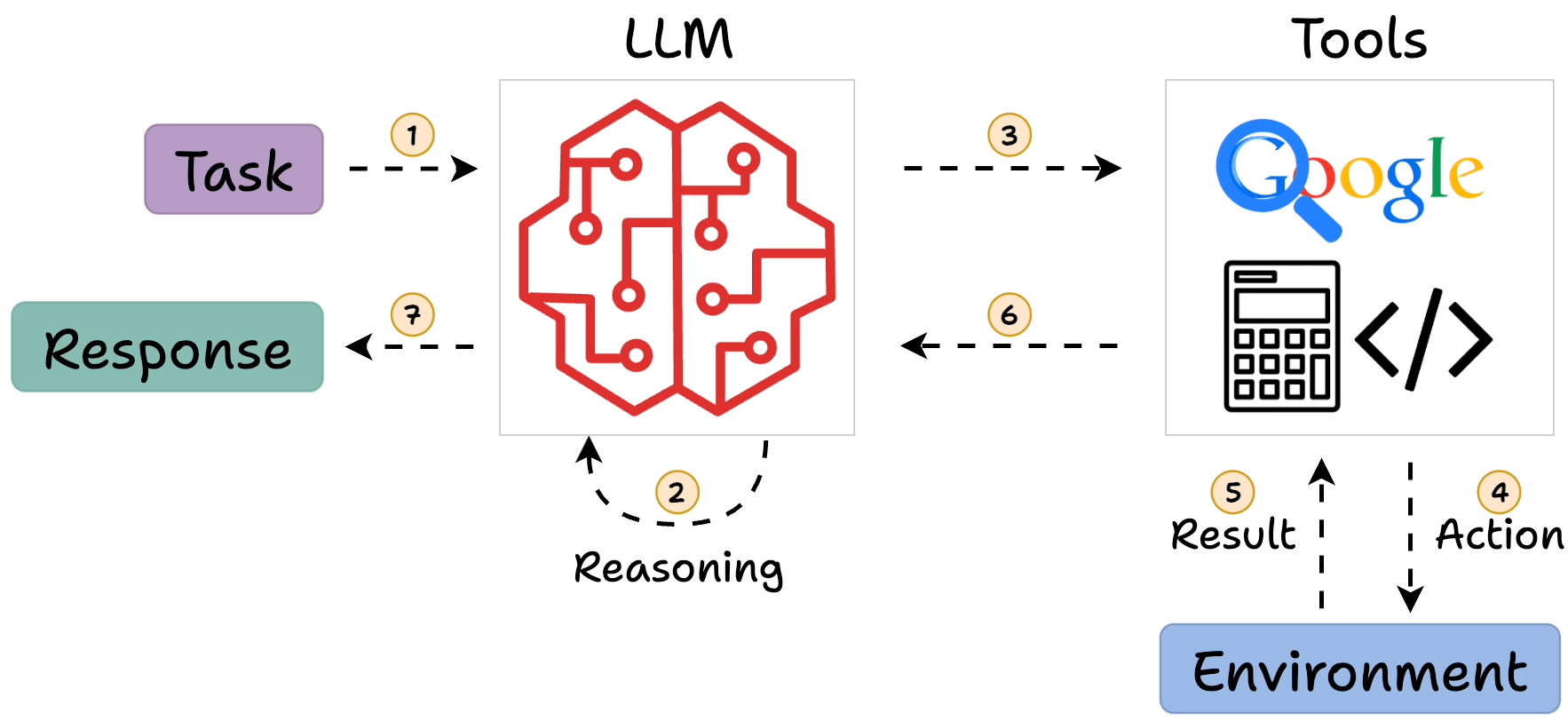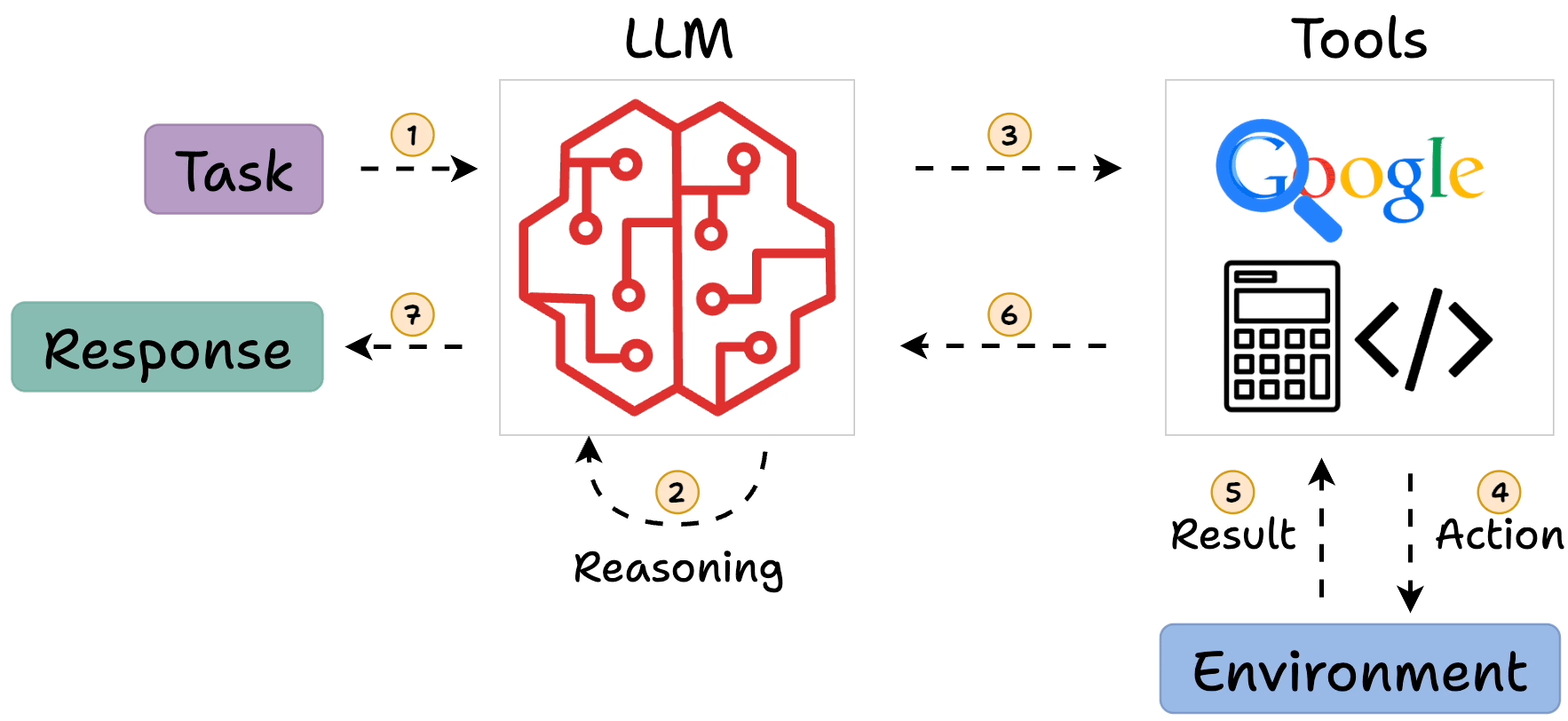
How ReAct Works
In ReAct, the LLM generates a “thought” to plan, selects an “action” from available tools, observes the outcome, and iterates. This loop continues until the model outputs a final answer. For example, answering “What is Olivia Wilde’s boyfriend’s age raised to the 0.23 power?” might involve searching for the boyfriend, then calculating the power.
 Source: Internet
Source: Internet
Key Points
- ReAct Framework: It seems likely that ReAct is a prompting technique enabling LLMs to alternate between reasoning (thinking step-by-step) and acting (using tools like searches or calculations), improving accuracy on complex tasks by reducing hallucinations and incorporating external information.
- Core Process: Evidence leans toward a loop of Thought (reasoning), Action (tool invocation), Observation (results), repeating until a final answer, mimicking human problem-solving.
- Benefits and Limitations: Research suggests ReAct enhances interpretability and performance on knowledge-intensive and decision-making tasks, though it may increase computational costs and rely on well-defined tools; it’s particularly useful for dynamic environments but less so for simple queries.
 Source: Internet
Source: Internet Source: Internet
Source: Internet